A Healthcare System’s Guide to Handling Data Breaches

As the medical profession continues to move away from paper documents and upgrade to digital files, protection against data breaches and hackers is becoming ever more important. In 2019 alone, massive companies such as Canva, Capital One, and Epic Games (the developer of Fortnite) reported data breaches that, combined, jeopardized well over 250 million people.
In the healthcare industry, data breaches don’t just mean emails and credit card information. Sensitive Personal Health Information is at risk of being stolen as well, making the stakes of cybersecurity even higher. When a hacker gets the best of your medical practice, how should you respond to make sure you stay compliant with HIPPA and cybersecurity laws? What sort of patient communications need to be distributed? How can you recover patient trust after a serious data breach?
Cybersecurity is complicated, but the clean-up after a data breach is even more complex. Some of the true costs associated with data breaches are:
- Countless employee hours spent on the investigative process, cybersecurity upgrades, patient communications, and general stress.
- Legal fees associated with high value yet incredibly expensive law firms that have experience with data breaches.
- Potential fines, especially if the cause of your data breach was faulty or outdated security software.
After realizing your organization might be the victim of a data breach, here are three key steps to take.

Determine the Cause
According to the HIPAA Journal, 40% of May 2020’s data breaches were caused by hackers. But a hacker is just one of the ways that sensitive health data can be stolen from your healthcare organization. An internal employee could accidentally or purposefully mismanage digital files, either through improper disposal or loss.
If your healthcare organization works with third-party vendors that handle PHI, there’s also the possibility that your vendor is the cause of your data breach. Not only does this make the solution and legal process more complicated, but it also means you should re-examine what cybersecurity features your vendors use and whether your organization’s security priorities align with theirs.
Work With a Legal Expert to Identify Options
Seeking legal counsel and potentially going to court over a class action lawsuit can be incredibly expensive for your organization. But similar to weighing the upfront cost of security software against the risk of a data breach, the cost of legal counsel will be worth it if it means staying compliant with federal cybersecurity regulations. There are many law firms that have experience in representing large, high-profile health networks when data breaches happen. Even if a lawsuit never occurs, lawyers can help you navigate the data breach — which is hopefully the first such incident for your medical practice.
As your lawyers will tell you, it’s vital to document each step you take throughout the breach process. Should a class action lawsuit occur, you’ll be thankful you recorded your handling of the incident. Seeking legal counsel early minimizes the chance of missing a step. And just like with cybersecurity software: better safe than sorry.
Communicate Early and Honestly
The HIPPA Breach Notification Rule requires all healthcare organizations to report a data breach within 60 days if over 500 individuals are affected. While silence might seem preferable in the short run, healthcare organizations can face serious fines (not to mention a PR disaster) if they fail to disclose their data breach.
In crisis communication, it’s important to release a statement that is not only truthful but also demonstrates a commitment to taking preventative action in the future. Facilitate collaboration between your legal team and your media relations team. Together, these people can craft a statement that satisfies HIPAA requirements and uses tactful and on-brand tone and verbiage. While communicating with your external vendors might not be explicitly required by the HIPPA Breach Notification Rule, sending a similar letter to these businesses could help them align their cybersecurity software and priorities with yours.
Trust Building and Damage Control
A data breach can cause a serious loss of confidence in your medical practice, which can damage the relationships you’ve built with your medical practice, your patients, and even your employees for years after the incident. In addition to sending the required communications to your patients to stay HIPPA compliant, here are a few strategies that can help your business recover customer trust:
- Follow-up statement inserts — Your patients will want to know how your medical practice is responding to the current breach and what plan exists to prevent future breaches. Consider producing a quarterly statement insert that gives updates on your progress toward strengthening your practice’s cybersecurity measures.
- IT and security upgrades — Make sure all the software that your practice uses is not only up-to-date but also protected by trusted security software. This includes your computers’ default web browser (old browsers, such as Microsoft Explorer, no longer receive updates and are therefore much easier to hack into). While the upfront cost might seem high, the cost of a data breach will undoubtedly be higher.
- Vendor collaboration — Make sure your vendors are also prioritizing cybersecurity by taking similar actions. Specifically, be sure to work with third-party billing vendors that are committed to the responsible handling of patient PHI and financial information. Vendors should be HITRUST-certified, which demonstrates a professional and sustained approach to cybersecurity.
HITRUST Certification
A data breach could cost your medical practice millions of dollars. Even though taking preventative measures might seem premature or dramatic and not worth the money, the clean-up required after a serious data breach will cost you many multiples of what you’d spend on security software, as well as broken customer trust and countless working hours to sort out the damage.
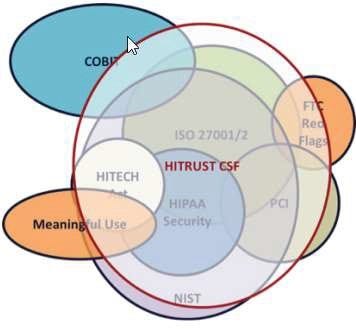
No matter the cause of your data breach, make sure you and your vendors are taking as many steps as possible to prevent data theft. HITRUST Certification maintains a common security framework by harmonizing all healthcare information security compliance standards. MailMyStatements was one of the first billing vendors to obtain HITRUST Certification. Because this certification must be renewed every two years after careful re-assessment and approval, HITRUST verifies that third-party vendors take a holistic, thorough approach to cybersecurity.
To avoid serious financial losses and damaged trust, be sure to work with a mailing and billing service that knows how to handle sensitive PHI.
Final Thoughts
Working with third-party service providers that perform a variety of functions, such as handling patient statements and patient payments, helps you navigate the increasing cost and complexity of running a healthcare practice, allowing you to improve cost-efficiency, augment the patient experience, and boost your bottom line.
To safeguard your patients’ interest while ensuring that your organization stays compliant to avoid hefty penalties and protect your reputation, you need to select vendors that are HITRUST-certified so you can rest assured that your patients’ sensitive information is in good hands.

Derek Griffin is the VP of Sales and Business Development for MailMyStatements. He has over 13 years of experience as a healthcare sales executive, is experienced in multiple healthcare related fields from front office to billing and collections, and has worked in various roles within Optum, a UnitedHealth Group company and AdvanecedMD. He loves spending free time with his wife and kids, whether it is coaching the soccer team, attending dance recitals, or fixing bikes.
You can follow Derek on Twitter @Derek_Griffin1


Comments
Post a Comment